
Microsoft has announced a coordinated legal action in the United States and the United Kingdom that has dismantled RedVDS, a...






Palo Alto Networks has issued security updates to address a high-severity denial-of-service (DoS) vulnerability affecting its GlobalProtect Gateway and Portal products, warning that the flaw can...


Security Operations Centers (SOCs) are under more pressure than ever in 2026. Threat volumes continue to rise, attacks are more sophisticated, and adversaries move faster than...

As AI copilots and assistants become deeply embedded in everyday business operations, security strategies have struggled to keep pace. Many organizations continue to focus primarily on...


A high-severity security vulnerability in the WordPress plugin Modular DS is currently being exploited in the wild, according to cybersecurity firm Patchstack. The flaw, identified as...
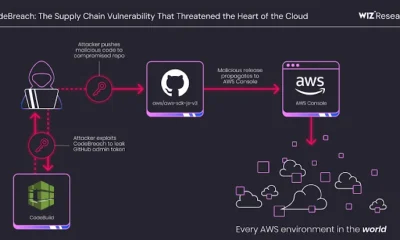

A critical misconfiguration in AWS CodeBuild exposed several high-profile GitHub repositories to potential supply chain attacks, according to cloud security researchers at Wiz. The vulnerability, dubbed...


Cybersecurity threats are evolving faster than ever, with attackers leveraging both old and emerging technologies to exploit vulnerabilities across IT, OT, and cloud systems. This week’s...


Cybersecurity experts have uncovered a critical vulnerability in AI chatbots like Microsoft Copilot, revealing a new attack method called Reprompt that enables data exfiltration with just...


Cisco has released urgent security updates to address a critical vulnerability in its Secure Email Gateway and Secure Email and Web Manager products after confirming active...


A China-linked cyber espionage group has been observed exploiting a previously unknown vulnerability in Sitecore software to infiltrate critical infrastructure organizations across North America, according to...


Cybersecurity researchers have uncovered a targeted espionage campaign aimed at U.S. government and policy-focused organizations, using politically charged content tied to U.S.–Venezuela relations to deliver a...
Recent Comments