Business
Skeletons in the IT Closet: Seven Common Microsoft Active Directory Misconfigurations that Adversaries Abuse
Published
4 years agoon
By
GFiuui45fg
The modern IT organization has a wide variety of responsibilities and competing priorities. As a result, cybersecurity is often overlooked in favor of projects that have an immediate impact on business operations. Unfortunately, this operating model inevitably leads to unaddressed vulnerabilities and security misconfigurations in services and Active Directory. We’ll refer to these unknown vulnerabilities and misconfigurations as “Skeletons in the IT Closet.” These skeletons are then leveraged by attackers to move laterally within a network and escalate privileges within the Active Directory domain.
In this blog, we explore seven of the most common system and Active Directory misconfigurations, how adversaries take advantage of them, and how IT and security teams can address them to strengthen their organization’s overall cybersecurity posture.
Misconfiguration 1: Administrative Privileges
Once an attacker has obtained initial access within an environment, the adversary will attempt to elevate privileges within the network. Adversaries typically have the goal of obtaining Active Directory Domain Administrator privileges, or, in other words, complete control over the Active Directory domain.
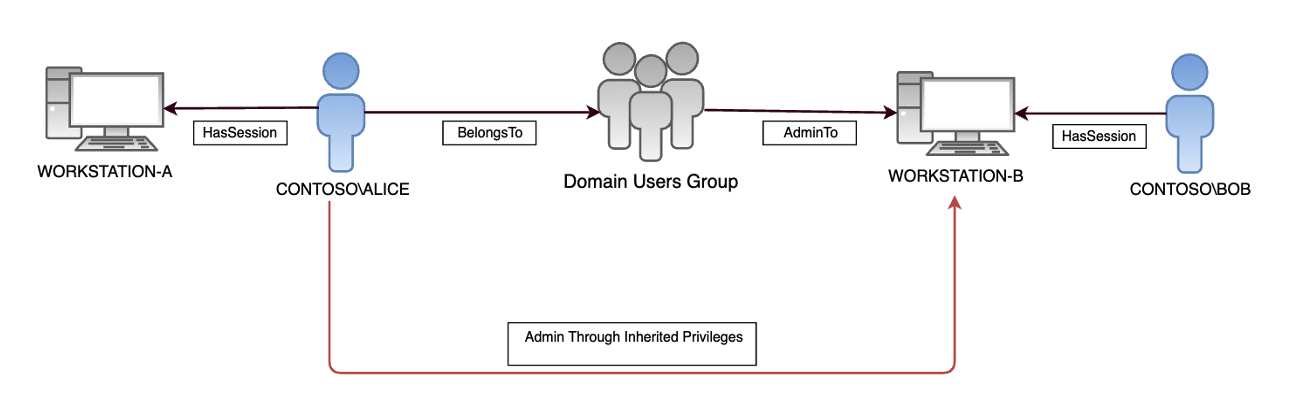
A common avenue to elevate privileges to Domain Administrator is through Active Directory misconfigurations. For example, Domain Users Active Directory group may sometimes assign administrative privileges to computer objects. The Domain Users group is a default group that all domain user objects inherit privileges from. Due to this inheritance, when the Domain Users group grants administrative privileges to a set of systems, usually all users in the domain have the same administrative privileges. CrowdStrike encounters this misconfiguration on about half of the red team exercises performed.
Example
An attacker has successfully phished a user, CONTOSO\ALICE, from the marketing organization on WORKSTATION-A. Alice does not have local administrator access over WORKSTATION-A (her workstation). However, due to the Domain Users group having administrative privileges over WORKSTATION-B, CONTOSO\ALICE inherits that privilege and also has administrative privilege on WORKSTATION-B. This allows the attacker to laterally move to WORKSTATION-B as CONTOSO\ALICE with administrative rights. With those administrative rights, the adversary can perform credential harvesting on WORKSTATION-B to obtain additional credentials and subsequent privileges within the Active Directory domain.
IT Action Items
IT and security teams should aim to limit administrative privileges to a small subset of users. Unless required, users should not have administrative privileges over their workstation. By limiting administrative rights to those employees who need them, IT and security teams can prevent cyber adversaries from escalating privileges within the Active Directory domain.
Many organizations are not fully aware of the privileges affiliated with the Domain Users Active Directory group. To identify them, organizations can utilize a tool like Bloodhound, created by @_wald0, @CptJesus and @harmj0y of SpecterOps to audit Active Directory relationships. BloodHound applies graph theory to Active Directory relationships, allowing IT personnel to easily identify unintended Active Directory relationships. It’s important to note that CrowdStrike has observed several cyber adversaries using BloodHound in intrusions. All BloodHound-related security alerts should be thoroughly investigated.
Misconfiguration 2: Network Shares
Network shares provide ample opportunity for an attacker to elevate privileges within a network. For example, in a previous red team assessment, CrowdStrike identified an unprotected network share that contained a writable IIS web root. This allowed CrowdStrike to write a web shell to the web root as a standard domain user and subsequently obtain code execution as the IIS process owner on the web server.
Further, open network shares often contain sensitive data that should not be available to standard domain users. This can include sensitive information spanning executive email backups, plaintext passwords, financial information and even corporate “crown jewels,” meaning the most prized data the enterprise protects.
To reduce the risk of exposing sensitive information or providing avenues for an attacker to escalate privileges, IT and security teams should take steps to identify and track all network shares within the domain. A tool like SharpShares, originally written by Dwight Hohnstein and expanded upon by Mitchell Moser, can be used to identify list, read and write network share permissions for a designated domain user. This utility is also compatible with Cobalt Strike’s execute-assembly module.
IT and security teams should leverage RBAC (role-based access control) and ACLs (access control lists) to restrict access to network shares and specific files. With RBAC, IT teams can restrict network share access to specific groups. ACLs provide additional granular control and allow specific permissions for a particular user or file.
IT Action Items
IT teams should proactively identify available network shares using SharpShares or an equivalent network share enumeration tool. RBAC and ACLs should be utilized to restrict access to the network shares and sensitive information within them.
Misconfiguration 3: Service Accounts with Weak Passwords
Adversaries will look to elevate their privileges within a network by compromising credentials of privileged accounts. It is common for service accounts to be granted administrative privileges to multiple hosts in an Active Directory environment.
Kerberoasting is an attack technique that attempts to obtain plaintext passwords from service account Kerberos tickets. One way to designate service accounts is through an attribute called a service principal name (SPN), which ties a service to a user account.
In a Kerberoasting attack, an adversary uses the SPNs that are tied to other service accounts and requests Kerberos tickets, which are encrypted with the service account’s password. This means that when a domain user requests a Kerberoasted ticket, the domain user actually receives a hashed version of a service account’s password. These tickets can be requested using tools like GhostPack’s Rubeus or SecureAuth Corporation’s GetUserSPNs.py. Requested tickets can then be extracted from the network and “cracked” to obtain the service account’s plaintext password using tools like Hashcat or JohnTheRipper.
Organizations can utilize BloodHound to identify privileged service accounts. The data gathered by BloodHound is stored in a neo4j database, which can be directly queried using Cipher query language. The two cipher queries shown below can help identify which service accounts are granted administrative privileges. The first query returns service accounts and sorts them by the number of hosts that have explicit or group-delegated local administrative privileges. The second query returns service accounts belonging to a specific Active Directory user group, which in this case is the Domain Admins group.
MATCH (c:Computer)
OPTIONAL MATCH (n1:User)-[:AdminTo]->(c) WHERE n1.hasspn AND n1.enabled
OPTIONAL MATCH (n2:User)-[:MemberOf*1..]->(:Group)-[:AdminTo]->(c) WHERE n2.hasspn AND n2.enabled
WITH COLLECT(n1) + COLLECT(n2) AS t,c
UNWIND t AS Admins RETURN Admins.name, Admins.serviceprincipalnames, COUNT(Admins)
ORDER BY COUNT(Admins)desc
MATCH p=(u:User {hasspn:true})-[r:MemberOf*1..]->(m:Group)
WHERE m.name CONTAINS "DOMAIN ADMIN" AND n.enabled
RETURN u.name, u.serviceprincipalnames
IT Action Items
Require users to create strong passwords, especially for those that have SPNs related to them. The IT team should also leverage a modern form of encryption for Kerberos tickets, such as AES, that is more difficult for adversaries to crack compared to legacy encryption algorithms like RC4.
Misconfiguration 4: Services Running on Hosts with Multiple Admins
As noted above, adversaries will look to elevate their privileges within the network by compromising credentials of privileged accounts. Although plaintext and hashed credentials may be stored within memory of processes like LSASS, most modern endpoint detection and response (EDR) solutions heavily monitor and prevent credential access through these processes.
An alternative method of credential access exists when services are configured to run under a user account. Passwords for these accounts can be extracted by any local administrator. This is due to the passwords being stored in the registry hives of LSA secrets. Local admins can elevate to SYSTEM privileges and decrypt the registry hive using tools like Secretsdump.py from the Impacket toolset. Secretsdump.py is a Python script written by SecureAuth Corporation that extracts plaintext credentials from system registry hives containing LSA secrets. Tools like AtYourService developed by Mitchell Moser can identify services running on remote hosts as domain users.
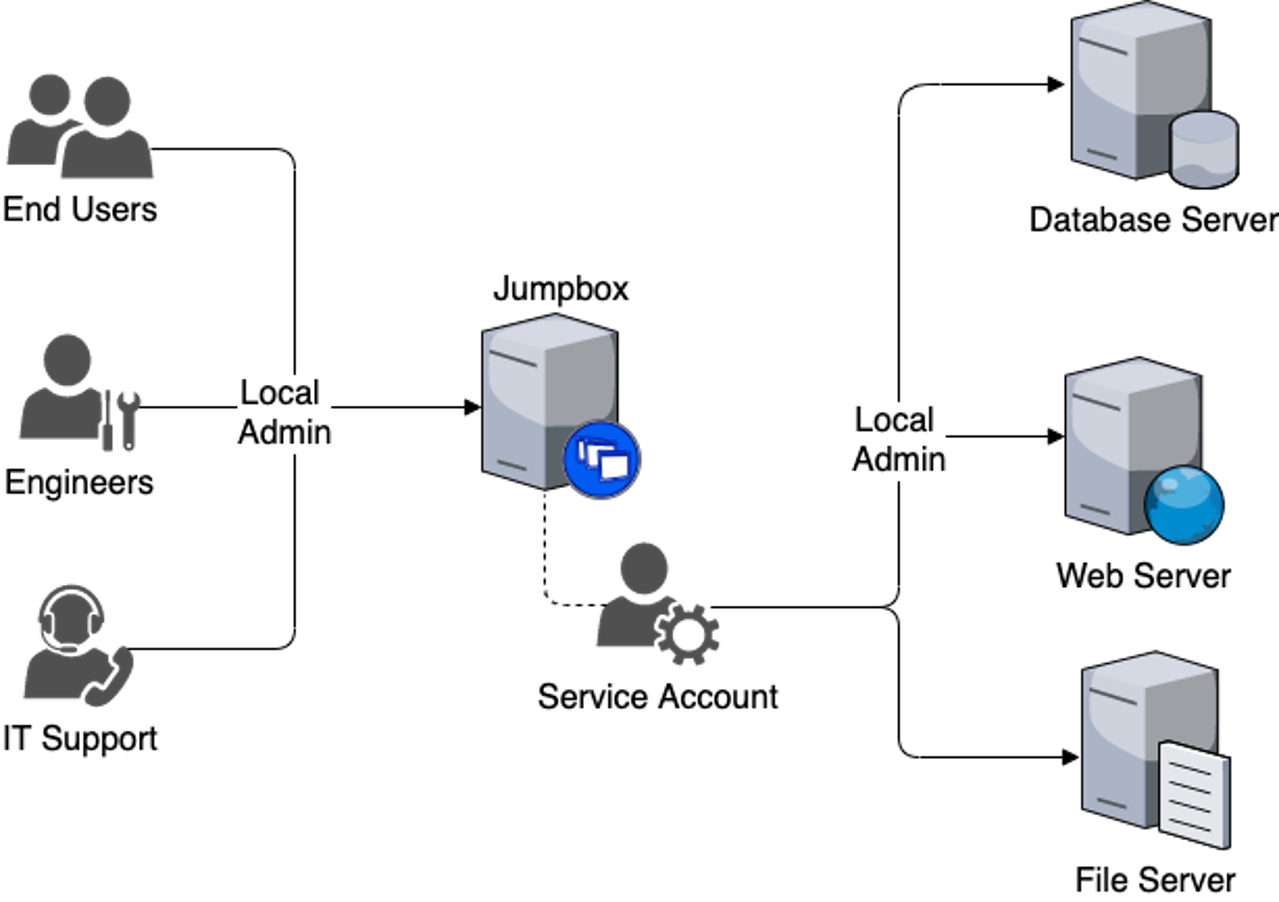
A common escalation path is outlined in the diagram below. In this scenario, multiple groups of users have been granted Local Administrative privileges to a host, which is used as a jumpbox. In the event that any one of these accounts is compromised, it can be used to extract plaintext credentials from the service account that is running on the jumpbox. This service account has additional Local Administrative privileges on other hosts on the network and allows an attacker to gain further privileges and lateral movement opportunities.
IT Action Items
IT teams should audit running services on hosts and ensure the principle of least privilege is enforced for any domain accounts configured to run services. Avoid granting service accounts excessive privileges on the domain. Additionally, IT teams should limit the amount of users that are granted Local Administrative privileges to a host. Any compromised account with Local Administrative privileges may be used to extract plaintext credentials for service accounts on a host.
Misconfiguration 5: Aged Accounts
As an attacker, aged accounts or accounts with no password expiration policy make ideal targets for adversaries looking to maintain long-term access to an environment. Aged accounts imply to an attacker that password rotation for the user account is either extremely difficult or not implemented for a particular reason — such as shared access among multiple users. Aged accounts may also exist due to lack of removing inactive or stale accounts, such as those of former employees or contractors.
Implementing and effectively enforcing a strong domain password policy prevents attackers from obtaining and maintaining access to valid credentials. Regularly rotating passwords can limit the amount of time an attacker can use credentials that they manage to obtain. Although many organizations have a strong domain password policy in place, often it is not universally enforced on all accounts in the domain.
IT Action Items
The IT team should audit Active Directory for outliers to the domain’s password expiration policy and identify stale accounts that have not been incorporated to a shared password management solution. Administrative accounts should be migrated into a privileged access management (PAM) solution and must be checked out and set to expire quickly — typically within 90 minutes or less.
Misconfiguration 6: Passwords, Passwords, Passwords
Active Directory environments present several avenues for credential access and abuse by adversaries. While other misconfigurations allow adversaries to gain unauthorized access to network resources and hosts using a single compromised account, credential-related attacks compromise additional accounts that may be used to further an adversary’s actions on objectives. Three routes commonly leveraged by attackers are identifying plaintext passwords, weak passwords with insufficient lockout periods, and password reuse.
Plaintext Passwords
Active Directory user objects contain a userPassword attribute that is typically used as a temporary field during user object password rotation. However, as a result of undocumented bugs and unexpected behavior in third-party password rotation services, this attribute can occasionally contain a user’s password in plaintext. CrowdStrike has not conclusively identified why the userpassword field is set or which products are responsible for not cleanly clearing the temporary field. Occasionally, CrowdStrike has seen this field contain a several-years-old password, or even an encoded or encrypted password.
Further, CrowdStrike has also observed plaintext passwords in the Active Directory user object description field. Using LDAP queries or a tool like BloodHound, an attacker can query across all user objects and filter the user object description field to identify a password.
IT Action Items
Ensure plaintext passwords are not included in the description or user password attribute for all user accounts.
Weak Passwords and Insufficient Lockout Periods
Adversaries may attempt to compromise additional accounts using easily guessable or shared credentials through a technique known as password spraying. Password spraying attempts to authenticate against numerous accounts using a single password.
Using this technique, attackers assume a lower risk of account lockout compared to brute forcing since each invalid authentication attempt will count as one failed attempt per account. Attackers looking to avoid operational impact to the target environment will be mindful of the organization’s lockout policy and exclude accounts that are near the lockout threshold. Password spraying tools for pentesters such as SharpHose from Mike Felch take into consideration the domain password policy, including fine-grained password policies, and each account’s badPwdCount attribute.
One key consideration for defending against this type of attack is setting an appropriate threshold for the lockout policy at the domain level. Ideally, the level should be low enough that attackers cannot make multiple authentication attempts within the lockout period but legitimate users are not inadvertently locked out of their account for a simple error. As such, it is also important to have a clear process for unlocking and resetting verified account users.
IT Action Items
IT teams should enforce strong, complex passwords that are not easily guessed, with an appropriate lockout policy for multiple failed authentication attempts. Defenders should also build a detection for login attempts to multiple accounts from a single host in a short time span. This is the clearest indicator of a password spraying attempt.
Password Reuse
Once an adversary has gained administrative privileges on a host, post-exploitation activities may include obtaining NTLM hashes for local accounts from the Security Accounts Manager, or SAM. (NTLM is an authentication protocol that leverages up to four messages to authenticate a client.) If the RID 500 local administrator account is enabled and configured with the same credentials across multiple hosts, adversaries can move laterally with privileged access to other systems through the compromised account.
Attackers with local administrator privileges can obtain these NTLM hashes by elevating to SYSTEM privileges and decrypting the SAM registry hive using tools like Secretsdump.py from the Impacket toolset or Mimikatz by @gentilkiwi. Once the NTLM hash has been obtained, the hash can be used to authenticate to other hosts using tools like CrackMapExec by @byt3bl33d3r or CredNinja by @raikia.
IT Action Items
IT teams should deploy the Microsoft Local Administrator Password Solution (LAPS) to ensure each RID 500 local administrator password is unique. In addition to having unique local administrator passwords, LAPS enables automatic rotation of passwords. Defenders can also build a detection similar to password spraying that looks for local authentication attempts to multiple systems from a single host within a short time span.
Misconfiguration 7: Legacy Systems
Legacy systems are a true skeleton in the IT closet for almost every organization. For example, an engineering team or product manager could inform the security team that a legacy system cannot be replaced for one more year due to a business-critical dependency. One year turns into 10, and soon there could be a Windows 2003 server sitting in production with no concrete plan to replace it.
Attackers target legacy systems due to the unpatched critical vulnerabilities that affect them. EternalBlue (MS17-010) and BlueKeep (CVE-2019-0708) are favorite vulnerabilities that are targeted on legacy systems as successful exploitation results in code execution in the context of the SYSTEM account, providing the attacker complete control of the vulnerable system.
Legacy hosts can be quickly identified by querying the Active Directory environment by operating system names. For example, you could use Mitchell Moser’s SharpLDAPSearch to identify Windows Server 2003 systems with the following query:
SharpLDAPSearch.exe "(&(objectCategory=computer)(operatingSystem=*2003*))" cn
IT Action Items
IT teams should perform an audit of Active Directory to identify legacy systems. Active Directory computer objects contain an operating system attribute that can be used to identify the operating system. Further, IT teams should ensure that identified legacy systems are integrated into the organization’s application lifecycle management and patch management programs. In doing so, the organization will be better prepared to anticipate and address end-of-life deadlines.
Legacy systems that cannot be upgraded to a supported operating system should be segmented from the rest of the environment and have extensive security measures to limit access over SMB and RDP.
Avoiding Common Misconfigurations
This post is based on our recent Fal.Con 2020 presentation, which explores these common system misconfigurations, how adversaries take advantage of them and how IT teams can address them to strengthen overall cybersecurity. For more information about these misconfigurations and others that may be lurking in your IT closet, please access a replay of our presentation here.

IoT security threats highlight the need for zero trust principles

New infosec products of the week: October 27, 2023

Raven: Open-source CI/CD pipeline security scanner

Apple news: iLeakage attack, MAC address leakage bug

Hackers earn over $1 million for 58 zero-days at Pwn2Own Toronto







