Cyber Security
Why so many cybersecurity attacks still start with an email
Published
3 years agoon
By
GFiuui45fg
While cybersecurity attacks are increasing across the many threat vectors, email still remains the most common channel for opportunistic and targeted attacks. As attackers continue to advance and increase their sophistication levels, legacy email security technologies no longer provide sufficient protection for organizations. This means that most companies remain highly exposed and, in many cases, are not aware that their security solutions are inadequate until they are breached.
Low detection rates mean missed malicious emails and high false positives impact business processes
Email security solutions are faced with the challenge of adequately protecting against many different types of advanced threats, including advanced phishing and spear-phishing attempts that leverage multiple evasion techniques, impersonation attempts, sophisticated ransomware attacks, account takeover, zero-day vulnerabilities and more.
The complex threat landscape, combined with the continued use of outdated technologies such as traditional sandboxes, results in low detection rates (as low as 60-70%). Consequently, too many threats manage to evade existing protections and land straight into user inboxes.
Many companies have accepted the reality that they may need to pay out to ransomware gangs or transfer money due to a BEC scam, but this should not be the norm. The actual sums are growing and have reached millions of dollars for ransomware and hundreds of thousands of dollars for BEC scams.
On the other hand, when email security solutions begin detecting legitimate emails as malicious, this can impact the business in multiple ways. The first is that important emails are not read by the intended users. Another issue is that users become disillusioned by the email security system and begin to ignore the verdicts, otherwise known as the boy who cried wolf syndrome, opening the organization to risks.
So, here are a few of the most significant pitfalls organizations face when securing their email channels and a few key tips to better protect your business.
Technology gaps affect detection rates
Many email security systems are not equipped with the necessary technology to detect the advanced threats that are becoming ever more sophisticated.
Packed programs hide malware
Packers are used by hackers to avoid detection by antivirus software. Packing malware makes it difficult for malware analysts to reach the original code and analyze it.
Relying on signatures is not comprehensive
Using standard antivirus programs to scan potential malware is a common first approach used in many security solutions. While this often works, this method does not succeed in all cases. These programs use databases containing suspicious code (also known as file signatures) that are used to identify potential malware. Sophisticated hackers easily evade these programs by modifying their code in a way that will not be detected by the antiviruses. In addition, new and rare code will not be identified if it is not already in the database.
Sandboxes are slow and bypassed
While this is a popular approach often used for dynamic scanning, advanced malware can provide challenges that a virtual machine may not overcome. For example, certain types of malware require command lines in order to be executed or are set to sleep for a time frame before beginning to execute commands. Sandboxes will not be able to run malware of this sort as they do not have command-line options and will often not wait long enough to detect the malicious command lines. These are a few of the drawbacks that might prevent malware from being detected in a virtual environment.
Limited system agility decreases the effectiveness of detecting new and advanced attack vectors
So why are security solutions’ detection rates low and, in many cases, deteriorate over time? In many cases, it is due to a system’s lack of flexibility to learn and adjust threat detection techniques and algorithms based on the changing attacks seen in the field.
Since the cyber threat landscape is rapidly evolving, any email security solution that protects against today’s attacks won’t necessarily protect against tomorrow’s attacks unless it has technology that is flexible and agile enough to support new logic and rules added by the vendor, customers’ IT administrators or SOC teams.
Many tout machine learning as the panacea to all malicious email campaigns, but the reality is that the combination of detection technology and expert incident response combined with the agility to easily adjust the email security system with policies and rules provide the highest detection rates with the lowest false-positive rates.
Understanding how attackers bypass your email security solution and the ability to immediately create new logic that supports catching those advanced scenarios in the future ensures optimal results.
The following are examples of how agile systems identify new patterns and can add new logic to help increase detection rates:
- The security solution can use blacklists to stop certain emails, but in the next wave of phishing attacks, emails might come from a new sender or even a legitimate sender. With a flexible email security solution, new logic and decisions can be dynamically deployed to instantly prevent these new attacks and the next ones as well.
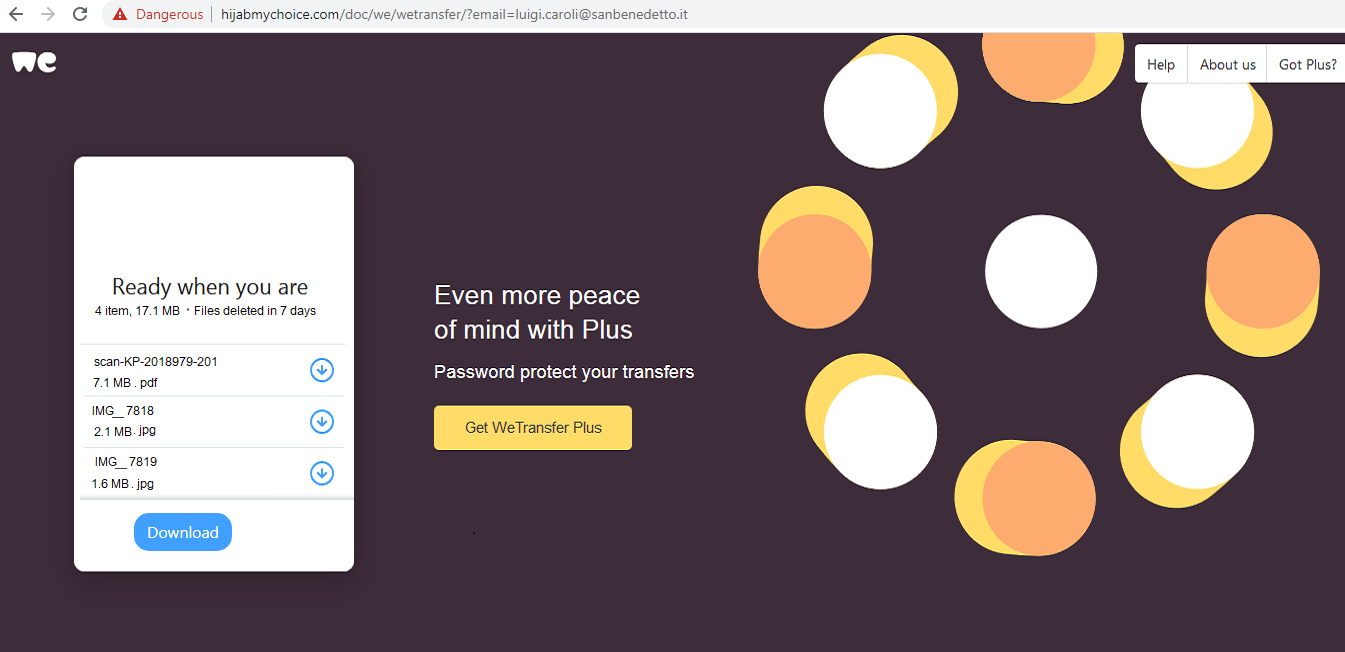
- Websites impersonating legitimate services like WeTransfer are used to transfer malicious files to users’ personal computers. In cases like this, attackers will often impersonate a legitimate WeTransfer page in the hopes that the victim will download the content, and by doing so, compromise his work or personal environment.
Phishing sites containing fake login pages are often used by attackers in an attempt to steal personal information, such as login credentials and payment details. Most phishing cases often impersonate popular brands often used in the work environment, such as Office 365.
Website builder tools like Weebly or Wix are providing attackers with free, quick and simple templates to build sites for attacks. For sophisticated illegitimate websites such as the ones below, the email security system should know how to identify them via technology such as image recognition as well as actually following and checking the active links on the site. The ability to add new logic, adjust image recognition capabilities and add new phishing site URLs to the detection mechanisms on the fly allow the interception of new emerging attack campaigns before they reach the inbox.
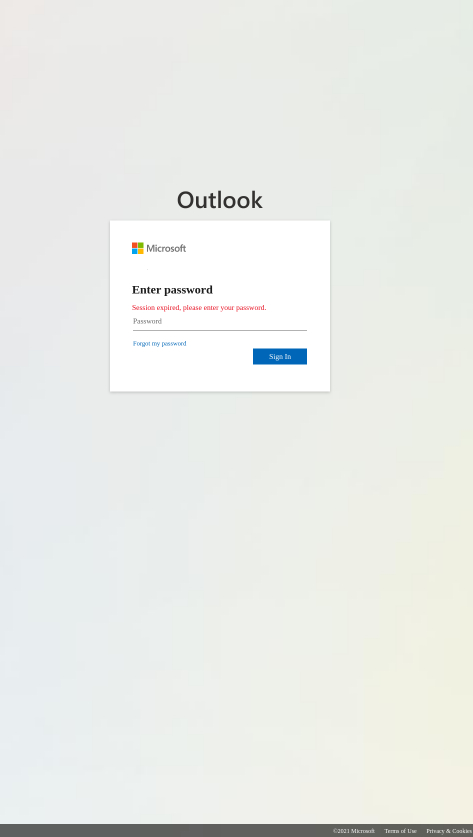
Images courtesy of Perception Point
Incident Response infrastructure and resources are lacking
To achieve the highest detection rates and lowest false-positive rates from your email security solution, good communication is essential between the organization’s IT and/or SOC team, the email security vendor and the end users. Bridging communication between these three parties is exactly the work of an Incident Response Team and why the team is so important in preventing deterioration of detection rates.
That being said, the work of an incident response team is challenging and requires expertise. It can be difficult for companies to dedicate sufficient in-house time and resources to properly manage the growing number of incidents. Many organizations have a long-term roadmap for this, but it requires sophisticated automation and integration between systems and can take companies months and even years to set up and deploy properly.
Even if an organization manages to set up its processes and systems and has a well-trained team in place for incident response, the team can still struggle with the demanding tasks of incident response such as:
- Monitoring, analyzing and reporting of all email security incidents 24-7
- Rapid alerts and analysis of malicious attempts
- Optimizing the security system’s engines for advanced scenarios
In many organizations, users will report a suspicious email. Because there are not enough resources to investigate each report, they are automatically pulled from the inbox and deleted. When this method is used, the organization cannot gain nor leverage the knowledge from the suspicious attacks that may have bypassed their system for continuous optimization.
A lack of visibility and KPIs make it difficult to measure how the system performs
KPIs that measure false positives and false negatives are important for an organization to understand the efficiency and accuracy of its email security system. Unfortunately, it’s not easy for a company to set up these KPIs. For example, how do organizations calculate and report the number/percentage of false positives shown by their solution?
Some solutions don’t provide this KPI et al. or allow an easy way to retrieve a false positive measurement. SOC teams only know that there are false positives if users ask them to release emails or ask IT why they didn’t receive an email they know was sent.
How do you measure false negatives? These are the malicious emails that bypass the email security solution, and some solutions do not provide a proper way to view these statistics. Often, a company intuitively “feels” that their email security solution is not performing effectively, but they don’t have the proof in their data. The main cause for the lack of visibility is that there isn’t effective handling of the flow of security incidents or proper support in email security solutions to retrieve the correct number of incidents.
Email protocols are messy and complex
Another challenge facing organizations and affecting their email security effectiveness is failing to properly configure their email protocols.
For example, the DMARC protocol protects organizations from email spoofing, phishing scams and other cybercrimes. However, a recent study shows that less than 50% of Fortune 1000 companies implement DMARC in their email. Imagine how few mid and smaller-size companies implement it.
Another point to consider is that even if an organization implements DMARC and does all it can to strengthen its email security, it can’t control the security level adopted by its business partner ecosystem. That’s why external companies users interact with often pose a great risk to the organization.
4 Tips on How Organizations Can Close the Email Security Gap
- Thoroughly evaluate email security solutions before selecting one to implement, and take the time to evaluate with a POC that will measure detection rates against the existing email security solution.
- Consider a flexible email security solution that enables the constant updating of the rules and logic for catching new and evolving threats and one that supports advanced scenarios.
- Improve communication between the IT and/or SOC team admin of the organization, email security vendor, and end users using a professional Incident Response team. This is key to achieving high detection rates closer to 100%.
- Implement DMARC, SPF and DKIM checks, and choose an email security solution that supports validating them. Include a risk assessment in your vendor selection process, and make sure you take measures in your email security solution to protect from riskier vendors.
A Look Towards the Future
In contrast with other channels, email security is more challenging to protect due to the reasons discussed in this article. With more than 300 billion emails sent around the globe daily, however, it is imperative that we work together as a global community to improve email security. Through cooperative efforts, we can close the security gap and build a more secure future for organizations across all industries.

IoT security threats highlight the need for zero trust principles

New infosec products of the week: October 27, 2023

Raven: Open-source CI/CD pipeline security scanner

Apple news: iLeakage attack, MAC address leakage bug

Hackers earn over $1 million for 58 zero-days at Pwn2Own Toronto