Business
What is Email Spoofing? – Email Threat Prevention Checklist 2023
Published
2 years agoon
By
GFiuui45fg
A deceptive method used by malicious individuals to send emails with fictitious sender information is email spoofing.
The attacker creates the impression that the email is coming from a reliable source, such as a reliable business or person, by changing the email’s header information, especially the “From” field.
By convincing recipients that the email is legitimate, this tactic hopes to get users to give private information, fall for phishing scams, or accidentally download malware.
Email spoofing focuses on taking advantage of the built-in flaws in the email protocol rather than hacking the sender’s email account.
It is crucial to be aware of strange emails, thoroughly check sender addresses, refrain from clicking on suspicious links or attachments, and put email authentication mechanisms into place in order to guard against email spoofing.
Email Spoofing Statistics
- Increasing Prevalence: For many years, email spoofing has been a common strategy for hackers. Due of its success in misleading recipients and getting over conventional email security measures, it is still a popular technique.
- Phishing Attacks: Email spoofing is typically linked to phishing attempts, in which attackers try to convince victims to divulge private information like passwords, financial information, or personal information. Millions of phishing emails are sent out every day, making phishing attacks an ongoing serious danger.
- Targeted Industries: Campaigns using email spoofing frequently target a variety of sectors, including financial institutions, healthcare providers, governmental entities, and e-commerce websites. Certain industries are chosen by cybercriminals as desirable targets because they handle sensitive data or have a sizable consumer base.
- Financial Impact: For both people and businesses, email spoofing can lead to significant financial losses. Businesses throughout the world have lost billions of dollars as a result of Business Email Compromise (BEC) frauds, which frequently use email spoofing. These frauds often prey on employees in charge of financial operations and deceive them into sending money that is not theirs.
- Impersonation Tactics: Trying to manipulate reputable entities, like well-known brands, service providers, or coworkers within an enterprise, is a common technique used in email spoofing. Attackers compose their communications with care and frequently employ social engineering strategies to win over their target’s trust.
- Mitigation Measures: Organizations and individuals have deployed a number of email authentication systems, including SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC, to prevent email spoofing (Domain-based Message Authentication, Reporting, and Conformance). These procedures work to ensure the legitimacy of emails and assist stop spoofing from getting through to recipients’ inboxes.
Examples of Email Spoofing
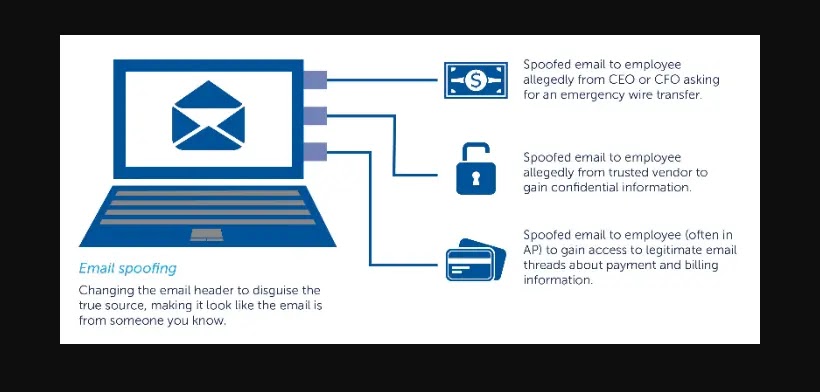
Here are a few examples of common email spoofing scenarios:
- Fake CEO or Executive Emails: Attackers may send emails to staff members, clients, or business partners while posing as senior leaders within an organization. These counterfeit emails frequently demand urgent acts, such as money transfers, the revealing of private information, or the beginning of unlawful transactions.
- Brand Impersonation: Spoof emails are used by cybercriminals to replicate well-known companies or well-liked internet services. In an effort to deceive people into disclosing sensitive information, these emails may notify recipients of a security breach, account suspension, or an urgent request for personal information.
- Financial Institution Scams: In phishing attempts, forged emails that seem to be from banks or other financial organizations are frequently employed. The emails can indicate that the recipient’s account has been compromised or that they must validate their login details by clicking on a dangerous link and entering personal data.
- Government Agency or Tax Authority Impersonation: Attackers may send spoof emails to people or businesses while posing as tax authorities or government entities. In order to collect sensitive financial or personal information, these emails frequently include threats of legal action, tax fines, or demands for quick payment.
- Password Reset or Account Verification Requests: The purpose of spoof emails is to trick consumers into changing their passwords or verifying their accounts by making them appear to be from reputable internet services, social media sites, or email providers. Typically, these emails contain harmful links that take visitors to phony websites intended to steal login information.
- Phony Job Offers: Job searchers may be the target of spoof emails that advertise tempting career prospects. Emails that request personal information, bank account information, or money for background checks or processing fees may appear to be from trustworthy businesses.
Organizations should adopt efficient incident response plans, regularly monitor email traffic for anomalies, and stay updated on emerging threats to stay ahead of the evolving email threat landscape with AI-powered solutions like Trustifi.
What needs to be Avoided in Email Spoofing
- Weak Email Protocols: Without strong authentication measures, email protocols like Simple Mail Transmission Protocol (SMTP) were created, making it simpler for attackers to modify the “From” field and send emails with faked sender addresses.
- Lack of Email Authentication: Strong email authentication techniques like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC are not commonly used by email servers and clients (Domain-based Message Authentication, Reporting, and Conformance). These procedures lessen the chance of email spoofing and assist in confirming the legitimacy of the sender’s domain.
- Phishing and Social Engineering: Attackers frequently use social engineering techniques to mislead victims into giving up private information or taking certain activities. They convince people to believe the fake emails and carry out the intended acts by assuming the identities of reputable companies and using psychological manipulation.
- Malware and Botnets: Large-scale email spoofing attacks can be carried out via malicious software and botnets. It can be difficult to identify the source of assaults when a botnet’s compromised computers are utilized to send out large quantities of faked emails.
- Open Relay Servers: Attackers may use email servers that have been improperly configured or insecurely secured as open relay servers. These servers enable email spoofing attacks by allowing unauthorized users to send emails without the required authentication.
- Domain Name System (DNS) Vulnerabilities: Attackers may modify a domain’s DNS records by taking advantage of DNS-related flaws or configuration errors. They can send faked emails from domains that appear authentic by changing the DNS settings, which allows them to redirect email traffic.
- Lack of User Awareness: People are more prone to fall for phishing scams if they are ignorant of email spoofing tactics and best practices. Attackers count on receivers not thoroughly examining email data and believing the apparent sender without checking its legitimacy.
Methods to Identify Spoofing Email
Identifying spoofed emails can be challenging as attackers employ various techniques to make them appear legitimate. However, there are some methods you can use to help identify potential spoofing attempts.
Email security leader Trustifi employs AI algorithms to detect, Spoofing emails, unauthorized access, compromised accounts, or unusual email activity, alerting users to security risks.
Here are a few tips:
- Check the Sender’s Email Address: Look closely at the email address of the sender. The domain name or sender’s name in spoof emails frequently has subtle variations or misspellings that may go unnoticed at first sight. It should be compared to the legitimate email addresses you have on file.
- Verify Email Headers: The origin of an email is fully disclosed in the email headers. You can look for irregularities in the email headers, such as mismatched domain names or IP addresses that don’t correspond with the claimed sender.
- Analyze the Email Content: Take close attention to the email’s usage of words, grammar, and tone. Spelling errors, poor grammar, or an urgent and aggressive tone all be signs of a spoof email. Professional communication standards are often upheld by legitimate organizations.
- Hover Over Links: Do not directly on any of the email’s links. To see the underlying URL, simply move your mouse cursor over the link. Check to see if the link links to the correct location or if it takes you to a suspicious or unrelated website. Be wary of URLs that are shortened or have strange domain names.
- Look for Unusual Requests or Urgency: Emails that have been forged frequently ask recipients for private information, money, or fast action. Be cautious of emails that ask for personal information that the sender should already have, demand urgent responses, or make threats against you if you don’t comply.
- Cross-Reference with Known Contacts: Before acting on an email that seems to be from someone you know, think about getting in touch with them via a separate channel of contact to confirm the email’s validity.
- Enable Email Authentication: Verify that SPF, DKIM, and DMARC email authentication standards have been applied by your email provider or company. These techniques can assist in identifying and removing forged emails.
- Use Anti-Spam and Anti-Phishing Software: Activate and keep your email client’s spam and phishing filters updated. The likelihood of falling for spoofing attempts can be decreased by using these filters to recognize and warn against questionable emails.
- Trust Your Intuition: Trust your intuition if anything seems strange or too good to be true. When in doubt, err on the side of caution and avoid responding to emails until their legitimacy has been confirmed.
By employing machine learning techniques to detect anomalies in email communications, Trustifi helps To prevent users from falling victim to Spoofing attacks.
Motivations Behind Email Spoofing
The motivations behind email spoofing can vary depending on the goals and intentions of the attacker. Here are some common motivations observed behind email spoofing:
- Phishing and Identity Theft: Spoofing emails is a common component of phishing campaigns. Attackers send spoof emails to recipients in an effort to get them to give sensitive information such as passwords, credit card numbers, or personal information. The exploitation of this information for financial fraud, identity theft, or other illegal crimes is then possible.
- Financial Fraud: Spoof emails can be sent to trick recipients into providing banking information or engaging in financial transactions. Attackers may assume the identity of a company leader, a financial institution, or a business partner in order to convince victims to transfer money to fraudulent accounts.
- Malware Distribution: Malicious attachments or viruses can be distributed through email spoofing. Attackers trick recipients into opening phishing emails that include malicious files, such as documents with macros or executable programs. When these attachments are opened, malware may be installed on the recipient’s device, giving attackers access or control without authorization.
- Social Engineering and Impersonation: Attackers can pose as people or trustworthy entities, such as coworkers, friends, or superiors, using email spoofing. They can persuade recipients into carrying out certain acts or disclosing private information by taking advantage of trust and authority, frequently for financial gain or other malicious ends.
- Reputation Damage: Spoofing emails can be used to harm someone’s or an organization’s reputation. Attackers may send harmful or offensive emails from spoof addresses with the goal of harming the target’s reputation.
- Disruption and Sabotage: Email spoofing can also be used as a sabotage or disruption technique. With the purpose of creating confusion, miscommunication, or turmoil within a company or community, attackers may send fake emails with incorrect information or misleading instructions.
FREE Demo
Deploy Advanced AI-Powered Email Security Solution
Implementing AI-Powered Email security solutions “Trustifi” can secure your business from today’s most dangerous email threats, such as Email Tracking, Blocking, Modifying, Phishing, Account Take Over, Business Email Compromise, Malware & RansomwareFree Demo
Best Practices and Tips to Avoid Email Spoofing
- Enable Email Authentication: SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC should be used as email authentication systems (Domain-based Message Authentication, Reporting, and Conformance). These measures lessen the possibility of getting faked messages and assist in confirming the legitimacy of incoming emails.
- Verify Sender Information: Check the display name and email address of the sender. Watch out for tiny changes, misspellings, or domains that aren’t the sender’s actual domain. If unsure, check with known contacts or get in touch via a different communication channel to confirm the sender’s identity.
- Be Cautious of Unexpected Emails: When you get unexpected or unwanted emails, be wary, especially if they ask for personal information, money, or immediate action. Be wary of emails purporting to be from reputable companies, financial institutions, or governmental bodies because attackers frequently spoof these organizations.
- Don’t Click on Suspicious Links or Attachments: When opening links or downloading files from emails that seem suspicious or are sent by unknown sources, use caution. When you hover your pointer over links, look for any odd domain names or errors in the underlying URL.
- Be Vigilant with Personal Information: When sending personal information over email, use caution. Sensitive data is rarely requested by email by trustworthy organizations. Passwords, Social Security numbers, credit card information, and other sensitive data should never be shared without first confirming the email’s legitimacy.
- Educate and Train Employees: Businesses should regularly train staff members and educate them about email security, including email phishing dangers and how to spot fraudulent emails. The IT department should be notified of any phishing attacks or suspicious emails that are thought to have been sent.
- Implement Anti-Spam and Anti-Phishing Filters:Use spam filters and email security tools that can assist in identifying and removing phishing or harmful communications. Before they reach your inbox, these technologies can assist in blocking or quarantining suspicious messages.
- Keep Software and Systems Updated:Make sure your operating system, antivirus program, and email client are all up to date. Patching security flaws and defending against known exploits used in email spoofing attacks are made possible by regular upgrades.
- Exercise Caution on Public Wi-Fi Networks: Remember that public Wi-Fi networks could be insecure and vulnerable to man-in-the-middle attacks while using them to access your email. When using public Wi-Fi, avoid accessing private emails or signing into accounts that have financial or personal information.
You may like

IoT security threats highlight the need for zero trust principles

New infosec products of the week: October 27, 2023

Raven: Open-source CI/CD pipeline security scanner

Apple news: iLeakage attack, MAC address leakage bug

Hackers earn over $1 million for 58 zero-days at Pwn2Own Toronto







