

In this Help Net Security interview, Slava Bronfman, CEO at Cybellum, discusses approaches for achieving product security throughout a device’s entire lifecycle, fostering collaboration across business units...
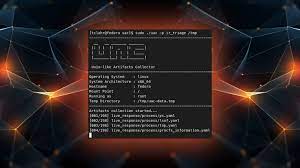

Unix-like Artifacts Collector (UAC) is a live response collection script for incident response that makes use of native binaries and tools to automate the collection of...


JumpCloud, a US-based enterprise software firm is notifying several customers of an “ongoing incident.” As a caution, the company has invalidated existing admin API keys to...


Although cyberattacks have become more common, handling them remains extremely challenging for organizations. Even if things go well on the technical level, incident response (IR) is still a...

You may already have an IR plan but regardless of how thorough you might feel it is at this moment, the evolving cyber threat landscape and shifting circumstances...

Visibility is always a priority, but it’s vital when responding to an incident. Time is always working against incident responders. Looking through rows of text data and...


The managed IT services market is growing both in size and importance, as more organizations decide it makes fiscal and operational sense to outsource key functions....


If your business has moved toward off-premises computing, there’s a bonus to the flexibility and scalability services that AWS and Microsoft 365 can provide. Incident response (IR) in...


Security researchers are warning that hackers can abuse online programming learning platforms to remotely launch cyberattacks, steal data, and scan for vulnerable devices, simply by using...


Deepwatch released the State of the Modern SOC report, which found that most IT security professionals believe they could have stopped business impacting cyber events if...
Recent Comments