

A freshly fixed vulnerability (CVE-2022-42889) in the Apache Commons Text library has been getting attention from security researchers these last few days, worrying it could lead...
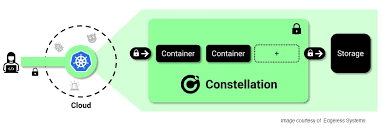

Confidential Computing is a hardware-based technology that shields computer workloads from their environments and keeps data encrypted during processing. In this Help Net Security video, Felix...


Oxeye researchers discovered a severe vm2 vulnerability (CVE-2022-36067) that has received the maximum CVSS score of 10.0. Called SandBreak, this new vulnerability requires R&D leaders, AppSec...


It’s hard to write good API specifications, and since most API gateways use them as IAC, they should be carefully checked for common mistakes. Writing an...


Success would depend to a significant degree on whether agencies require vendors of information and communications technology to provide a software bill of materials with their...


Fuzz testing helps developers protect their applications against memory corruptions, crashes that cause downtime, and other security issues, including DoS and uncaught exceptions. Code Intelligence has...


Multiple npm packages published by the crypto exchange, dYdX, and used by at least 44 cryptocurrency projects appear to have been compromised. Powered by the Ethereum blockchain, dydX is a...


Wolfi is a new community Linux undistribution that combines the best aspects of existing container base images with default security measures that will include software signatures...


Anaconda released its annual 2022 State of Data Science report, revealing the widespread trends, opportunities, and perceived blockers facing the data science, machine learning (ML), and...


North Korean hackers are using trojanized versions of the PuTTY SSH client to deploy backdoors on targets’ devices as part of a fake Amazon job assessment....
Recent Comments