

Medibank, Australia’s largest private health provider, has confirmed that last week’s “cyber incident” has resulted in a data breach. “Medibank has been contacted by a criminal claiming...


PhishLabs by HelpSystems has identified attackers leveraging a weakness in Google’s ad service to carry out phishing campaigns on financial institutions. In this Help Net Security video, Kevin...


While knowing full well that human lives may be at stake, criminal gangs have been increasingly targeting the healthcare sector with high-impact attacks like ransomware. 1. Tighten up...
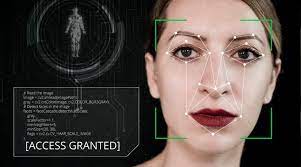

The term “deepfake” is used for photo, video or audio content that has been manipulated to make it seem that the subject is doing or saying...


Cybersecurity measures are increasingly failing to close gaps, and the healthcare industry, in particular, has become a high-dollar target due to limited budgets and quick ransom pay-offs....


Attacks against governments are nothing new. They have been an interesting target since they have existed, for the mere reason that not everyone agrees on how things...


IT leaders around the world share a ubiquitous appetite for greater network visibility. The findings of a Forrester Consulting study underscore a convergence in security with...


Access control is the heart of data protection. Striking the right balance between easy access and tight security isn’t easy, but getting it right is how...


In this Help Net Security video, Alon Levin, VP of Product Management at Seraphic Security, explains what social engineering is, and how prevalent it is. He offers...


https://player.vimeo.com/video/752049993?h=beb7669956&badge=0&autopause=0&player_id=0&app_id=58479&dnt=1 In this Help Net Security video, Chip Gibbons, CISO at Thrive, illustrates the differences between a business continuity plan and a disaster recovery plan. While these...
Recent Comments