

Threat actors are well-aware of the vulnerability of our cloud infrastructure. The internet we have today is not equipped to serve the data needs of the future. When...


As technology advances, more and more organizations are turning to cloud computing as a necessary solution for their data storage and processing needs. Cloud computing is...


Treasury’s Inspector General found the IRS did not meet requirements like malicious code protection and timely risk mitigation. The IRS’s Enterprise Case Management System did not...


Treasury’s Inspector General found the IRS did not meet requirements like malicious code protection and timely risk mitigation. The IRS’s Enterprise Case Management System did not...


An audit conducted by the Defense Department’s inspector general found agency components “may be unaware of known vulnerabilities and cybersecurity risks associated with operating their systems...


The Kinsing malware is now actively breaching Kubernetes clusters by leveraging known weaknesses in container images and misconfigured, exposed PostgreSQL containers. While these tactics aren’t novel,...
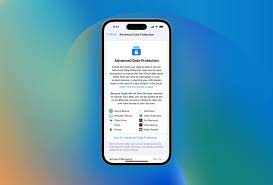

Apple is expanding end-to-end encryption options for users and finally offering E2EE for their iCloud backup. Advanced Data Protection for iCloud “iCloud already protects 14 sensitive...


The Pentagon has awarded its JEDI cloud contract replacement. The Pentagon on Wednesday announced the awardees of the Joint Warfighting Cloud Capability—or JWCC—contract, with Amazon Web Services, Google,...


“Russian missiles can’t destroy the cloud,” Ukraine’s minister of digital transformation explained. LAS VEGAS—Last February, with Russian military forces bearing down on its nation, the Ukrainian...


In this interview with Help net Security, Brad Jones, VP of Information Security at Seagate Technology, talks about cybersecurity trends organizations will be dealing with soon, particlularly concerning cloud...
Recent Comments